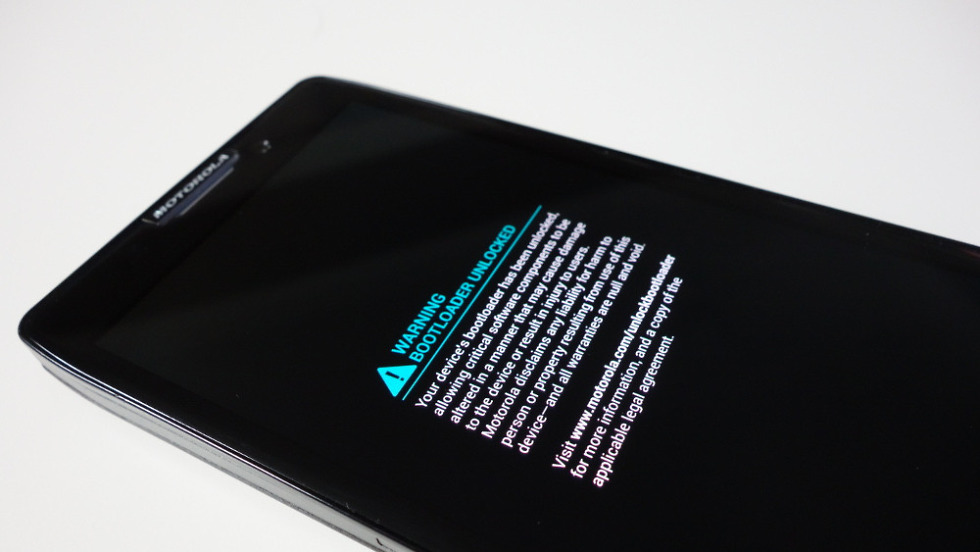
The Blackhat 2014 conference is taking place this week in Las Vegas, a conference which Dan Rosenberg, the man responsible for exposing numerous security exploits on Android devices, is speaking at. You may recall his previous work that unlocked the bootloader of a number of Motorola DROID devices, something that developers had attempted for years to try and accomplish without success.
When Rosenberg (@djrbliss) first popped up on the list of Blackhat conference speakers with a topic that was to conclude by discussing an unpublished security exploit “including a live demonstration of using it to permanently unlock the bootloader of a major Android phone,” we were certainly interested. His talk happened last night, and according to those at the conference, he successfully unlocked the bootloader of the Moto X on stage.
The security vulnerability was discovered in ARM’s TrustZone, which Qualcomm uses as a “system-wide approach to security” on devices using its Snapdragon processors. According to Rosenberg, this vulnerability exists in “all known Android devices that support TrustZone and utilize a Qualcomm Snapdragon SoC.” Well, except for the Galaxy S5 and HTC One (M8), both of which have been patched. Rosenberg also notes in a written report about the exploit that many more devices may have been patched by now through software updates. He first wrote this report up on July 1, but is only now showing it off a month later.
As for the Moto X being used to demonstrate his findings, this could mean that Motorola has yet to patch it. Then again, we have seen a number of updates arrive for Motorola devices within the last few weeks, most of which involve security on some level.
Other vulnerable devices specifically noted in this report include the Galaxy S4, Galaxy Note 3, Nexus 4, Nexus 5, G2, and original HTC One (M7).
So what does this mean for the future of unlocking your current phone? Well, it could mean nothing. As mentioned above, Dan wrote up his report on July 1, so manufacturers could have (likely have) seen it already. Since devices like the Galaxy S5 and One (M8) have been patched, it could mean that others will be patched (if they haven’t been already) before long. We would also need to Dan to release the full exploit and method, which I do not believe he has done, other than with a description of how it works. I sort of doubt that he is going to put together a 1-click button for making this happen. Instead, it will be up to other developers to take his findings and make some magic happen.
His report has been posted here.
Update: Qualcomm reached out to us with the following statement–
“Qualcomm Technologies takes the security of its products very seriously and invests to identify and address security vulnerabilities in our software before it’s made available to customers. We’re aware of this issue and have already made available software updates for our impacted customers to address the reported vulnerabilities.”

Collapse Show Comments97 Comments