Over the weekend, an exploit was found within Samsung’s Exynos processor that powers many devices, including the new Galaxy S3 and Galaxy Note 2. The exploit, if used by a malicious application, could potentially take control of the device’s RAM, which would spell serious trouble for owners.
Samsung has acknowledged the “potential security issue” and plan to provide a software update very soon to fix the issue:
Samsung is aware of the potential security issue related to the Exynos processor and plans to provide a software update to address it as quickly as possible.
The issue may arise only when a malicious application is operated on the affected devices; however, this does not affect most devices operating credible and authenticated applications.
Samsung will continue to closely monitor the situation until the software fix has been made available to all affected mobile devices.
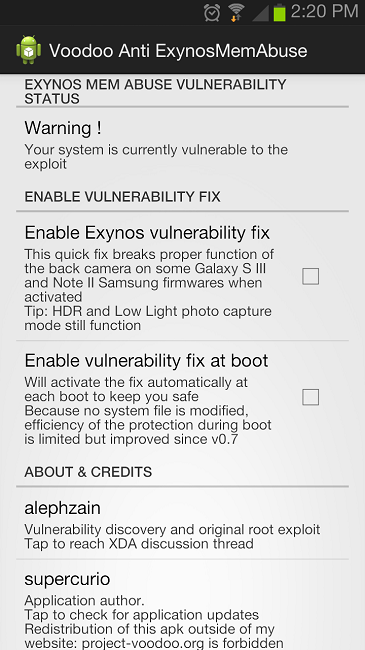
If waiting for Samsung to issue an official fix doesn’t sound good enough, then developers released a fix of their own until Samsung can catch up. An application, which does not need root access, can fix the exploit in seconds if you are worried about your device’s security. Feel free to download that here. All actions are completely reversible so don’t worry about hurting your phone.
Until then, stop downloading apps from untrustworthy sources.
Via: Android Central
Collapse Show Comments15 Comments